Today we are proud to announce our next major release 1.25.0.
What has changed?
We introduced a new scan level 1.1 to the scan that searches for PHP code hidden inside of image file names. It is a wide-spread tactic of attackers to hide malicious PHP code inside of image files that either contain dummy image data or no image data at all.
For example:
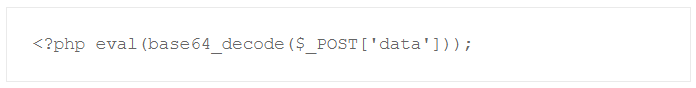
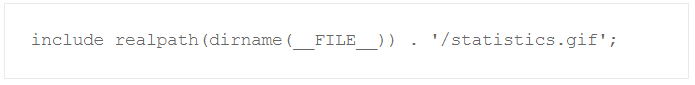
This short eval (evil!) code snippet would raise attention fast when found in a PHP file. But what if it is stored as statistics.gif and then there is this in the main php file:
Those lines of code are often overread when searching for obvious infections.
Furthermore we improved some heuristic rules for malware scans, including our "Level-4-Scan" that is executed by using the --db-scan switch. E.g. it recognizes some hints of the currently wide-spread infection of WordPress instances by "Trollherten" through a security issue in the WP GDPR Compliance plugin (you sould update to latest version asap, by the way).
Malware example
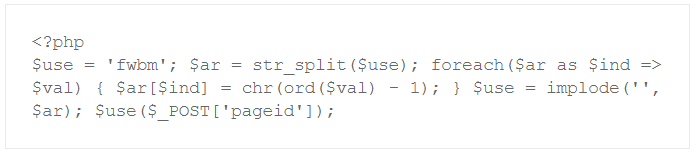
There is a new type of malware that raised our attention that hides it's malicious behaviour by shifting characters. Here is some simplified dummy code:
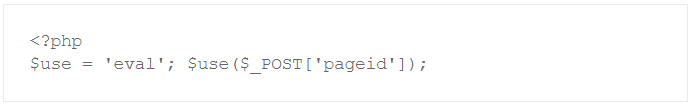
This is nothing else but
or even simpler
Marius Burkard has been working as a software developer for 20 years and has several years of experience as a server administrator. As one of the lead developers of the ISPConfig control panel and technical contact for several hundred web hosting customers, he has extensive experience with malware, hacked websites and the analysis of vulnerabilities.